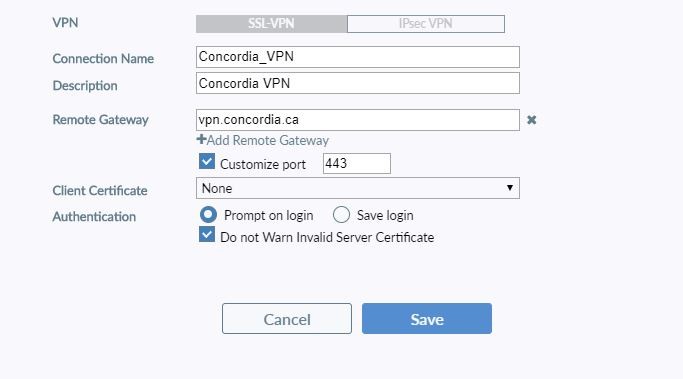
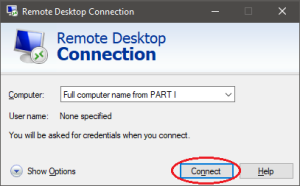
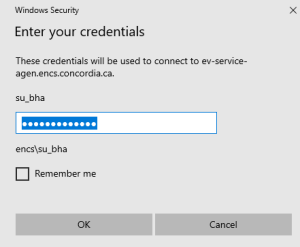
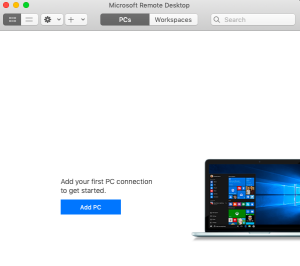
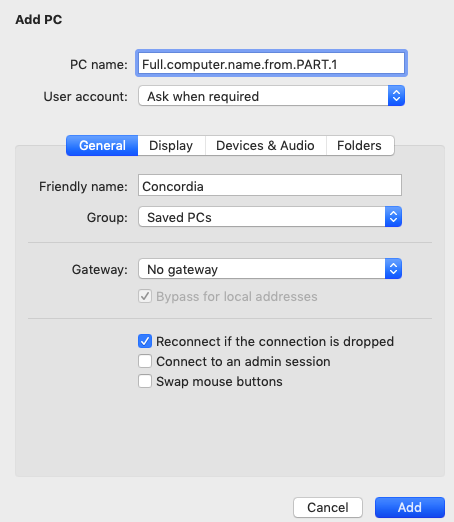
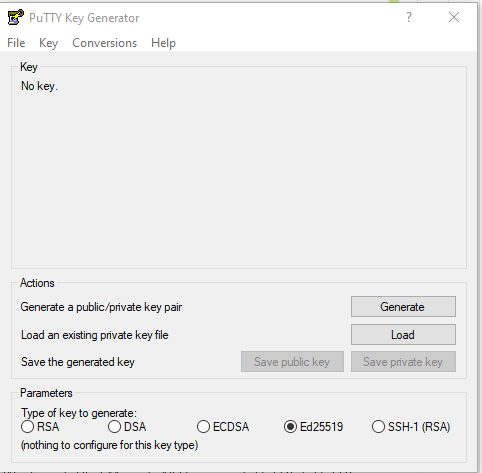
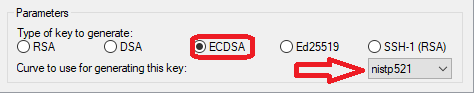
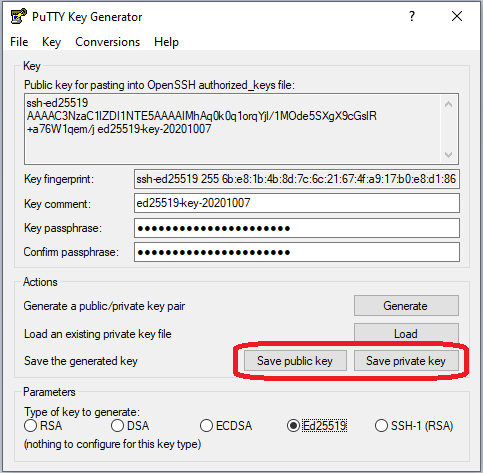
In Linux, Unix and Mac OS, the ssh-keygen tool can be used to generate ssh keys at the command line. To generate ssh keys using one of the elliptical curve signature algorithms, set the key type to either ed25519 (preferred) or ecdsa.
Commonly used ssh-keygen options for ed25519 type keys are:
ssh-keygen [-q] -t ed25519 [-C $comment] [-N $passphrase] [-f $keyfile]
Where the square brackets denote these optional items:
-q: quiets the program's usual output
-C: inserts a comment into the public key file
-N: new passphrase
-f: stores the new key in the given keyfile and the public key in $keyfile.pub
Examples:
A basic example:
ssh-keygen -t ed25519
An example which adds a comment, passphrase and saves the key to a specific location:
ssh-keygen -q -t ed25519 -C 'my new ssh key' \
-N 'a good passphrase' -f ~/.ssh/newkey
An example with ecdsa:
ssh-keygen -t ecdsa -b 521
where the -b flag determines the key length in bits and 521 is currently the largest option.
Note: Ed25519 keys have a fixed length and the -b flag will be ignored.
For more information about ssh-keygen, review the tool's man pages, e.g., enter man ssh-keygen at a linux prompt.
Copy the public key to the server
Once an SSH key has been created, the ssh-copy-id command can be used to install the key as an authorized key on the remote server, e.g., append the key to your user account's authorized_keys file in ~/.ssh/authorized_keys.
Example:
ssh-copy-id -i ~/.ssh/newkey user@host.encs.concordia.ca
For more information about ssh-copy-id, review the tool's man pages, e.g., enter man ssh-copy-id at a linux prompt.