- Add a comment and a unique key passphrase as needed
- Click on the Save Public Key and Save Private Key buttons to save your public and private keys.
How do I securely connect to a GCS server?
This document is written to assist faculty, staff and students of the Gina Cody School of Engineering and Computer Science (GCS) with valid user accounts, to configure their ssh clients to connect to GCS Public Access Servers or to a user managed server securely and without encountering warnings or errors.
Documentation
Before beginning the procedure below you will need to install an SSH client such as PuTTy
- Launch PuTTy
- In the Putty Configuration screen configure the following:
- Session:
- Set Host Name to login.encs.concordia.ca
- Activate the SSH radio button under Connection Type
- Optionally, enter a Saved Session name, e.g., login, and click on Save
- Session:
- Once you have configured your session, click the Open button.
- Enter your ENCS username and password when prompted.
To create an ssh connection with a GCS server, open up a terminal window and type the following at the prompt "ssh username@remotehost.address". Where username is your GCS username and remotehost.address represents the GCS server you wish to login to and run applications.
For example:
ssh a_user@login.encs.concordia.ca
Note:
In the above example, an ssh connection is created with login.encs.concordia.ca.
For a list of all GCS Public Access Servers and a description of their purposes, please visit the GCS Public Access Servers page.
FAQs
When generating SSH keys to authenticate to our systems, we recommend that your key pair(s) use one of the newer elliptical curve algorithms (ecdsa or the newer ed25519).
OpenSSH will be disabling the "ssh-rsa" public key signature algorithm by default in a near future release (as stated in the Release Notes for OpenSSH 8.4)
The following steps are for PuTTYgen, a key generator tool for creating pairs of public and private SSH keys. PuTTygen is one of the components of the open-source networking client PuTTy
- Make sure you have the latest version of PuTTy (available at https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html) installed to your system
- Launch PuTTygen
- Windows -> Start Menu -> All Programs -> PuTTY -> PuTTYgen
You will see the PuTTy key generator dialog box on your screen
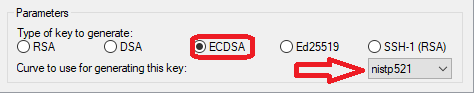
- In the Parameters field at the bottom of the diaglog box select either one of the two elliptical algorithm key types
- Ed25519 (recommended)
- ECDSA (Select the largest curve (521) when generating this key type)
- Ed25519 (recommended)
- Click on the Generate button to generate the keys
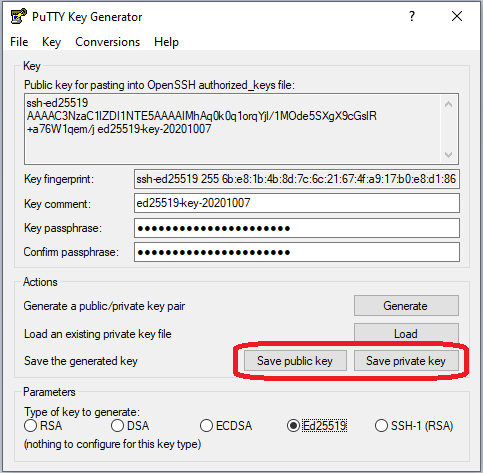
- In the Public key for pasting into OpenSSH authorized_keys file field at the top of the window be sure that the field starts with the text ssh-ed25519 (or ecdsa-sha2-nistp521).
- It will be necessary to move a copy of your public key to the server. The PuTTY User Manual regarding "Getting ready for public key authentication" provides detailed instructions on how to do so.
In Linux, Unix and Mac OS, the ssh-keygen tool can be used to generate ssh keys at the command line. To generate ssh keys using one of the elliptical curve signature algorithms, set the key type to either ed25519 (preferred) or ecdsa.
Commonly used ssh-keygen options for ed25519 type keys are:
ssh-keygen [-q] -t ed25519 [-C $comment] [-N $passphrase] [-f $keyfile]
Where the square brackets denote these optional items:
-q: quiets the program's usual output
-C: inserts a comment into the public key file
-N: new passphrase
-f: stores the new key in the given keyfile and the public key in $keyfile.pub
Examples:
A basic example:
ssh-keygen -t ed25519
An example which adds a comment, passphrase and saves the key to a specific location:
ssh-keygen -q -t ed25519 -C 'my new ssh key' \
-N 'a good passphrase' -f ~/.ssh/newkey
An example with ecdsa:
ssh-keygen -t ecdsa -b 521
where the -b flag determines the key length in bits and 521 is currently the largest option.
Note: Ed25519 keys have a fixed length and the -b flag will be ignored.
For more information about ssh-keygen, review the tool's man pages, e.g., enter man ssh-keygen at a linux prompt.
Copy the public key to the server
Once an SSH key has been created, the ssh-copy-id command can be used to install the key as an authorized key on the remote server, e.g., append the key to your user account's authorized_keys file in ~/.ssh/authorized_keys.
Example:
ssh-copy-id -i ~/.ssh/newkey user@host.encs.concordia.ca
For more information about ssh-copy-id, review the tool's man pages, e.g., enter man ssh-copy-id at a linux prompt.
Issue
The following error message is encountered when attempting to ssh or scp (which uses the ssh protocol) to a GCS server, e.g., login.encs.concordia.ca:
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ECDSA key sent by the remote host is
SHA256:mu5KXRR2xTlJXlLTJxKIGm2wprcF6ZUNS5YeSGvDMyg.
Please contact your system administrator.
Add correct host key in <user home>/.ssh/known_hosts to get rid of this message.
Offending RSA key in <user home>/.ssh/known_hosts:<line number in file>
ECDSA host key for <servername>.encs.concordia.ca has changed and you have requested strict checking.
Why you received this warning
During the summer of 2020, ssh ciphers on GCS servers were updated to a more secure protocol. Also for security reasons, GCS servers are configured to no longer accept DSA and RSA keys as those protocols are no longer considered secure.
Solution:
Update PuTTy to the latest version
- Visit https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
- Download the latest version of PuTTy (0.74 or later)
- Install
- Test by creating an ssh session with the <servername>.encs.concordia.ca
Important:
The minimum version of Putty that works with the newer elliptical curve ciphers is version 0.74.
Edit
~/.ssh/known_hosts(the file mentioned in the warning message) and remove the RSA key for <servername>.encs.concordia.caTest:
ssh <username>@<servername>.encs.concordia.ca
- Edit the file /Users/YOUR_MAC_USER/.ssh/known_hosts (with help of terminal using vi, vim or nano)
- Delete the line number mentioned in the error message as given below.
- Offending RSA key in <user home>/.ssh/known_hosts:<line number in file from warning message>
- Save and close the file
- Test to verify that the above steps resolved the error, e.g., in a terminal window, execute
ssh <username>@<servername>.encs.concordia.ca
Notes:
The term YOUR_MAC_USER refers to the name of your local mac account, e.g., the user name used to login to your mac computer.
